Wednesday, March 18, 2020
Friday, February 20, 2015
Qualcomm Facing $1B Potential Chinese Fine
Qualcomm Facing $1B Potential Chinese Fine
Posted by
Sam Churchill
on
Qualcomm could be hit with a fine as high as $1 billion, reports Fierce Wireless.
The San Diego-based company could also be forced to make concessions
that would negatively impact its licensing business. At least 30
foreign firms have come under the scrutiny of China’s 2008 anti-monopoly
law, reports Reuters. Qualcomm is the only major ongoing antitrust case in China involving a U.S. company and royalty fees.
Qualcomm’s prospects have been hampered by the National Development and Reform Commission’s (NDRC) 13-month investigation into the firm. An imminent decision in the case could force the company to pay fines potentially exceeding $1 billion and require concessions that would hurt its highly profitable business of charging licensing fees on phone chipsets that use its patents.
Qualcomm derives most of its profit from licensing fees and most of its revenue from sales of chipsets and modems. Qualcomm reportedly earned about half of its global revenue of $26.5 billion in China for the fiscal year that ended Sept. 28. Some observers believe that Qualcomm controls some 21% of LTE royalties.
President Barack Obama, during his recent visit to China, pushed his Chinese counterpart, Xi Jinping, on the use of Chinese antitrust policy to limit royalty fees for foreign companies. The push by Obama could alter China’s calculus on the issue, but it could just as well backfire. reports Fierce Wireless. It underscores the importance Washington places on China’s investigation.
The former deputy head of NDRC, Liu Tienan, was sentenced to life in prison earlier this month after convicting him of taking bribes and abusing his power, reports the NY Times.
China Mobile recently said it had 50 million LTE subscribers, with plans to have 150 million customers on the network by the end of next year and 300 million customers by the end of 2016. Their LTE network runs across a total of 130 megahertz of spectrum in the 1880-1900 MHz, 2320-2370 MHz and 2575-2635 MHz bands. China Unicom, the country’s No. 2 wireless carrier, said its 3G and LTE network attracted 4.9 million customers during Q3, while China Telecom, the country’s third-largest mobile operator, had 1.33 million LTE customers.
The latest edition of Ericsson’s Mobility Report predicts that 90 percent of the world’s population over six years old will have a mobile phone by 2020, with smartphone subscriptions forecast to top 6.1 billion by then.
Qualcomm’s prospects have been hampered by the National Development and Reform Commission’s (NDRC) 13-month investigation into the firm. An imminent decision in the case could force the company to pay fines potentially exceeding $1 billion and require concessions that would hurt its highly profitable business of charging licensing fees on phone chipsets that use its patents.
Qualcomm derives most of its profit from licensing fees and most of its revenue from sales of chipsets and modems. Qualcomm reportedly earned about half of its global revenue of $26.5 billion in China for the fiscal year that ended Sept. 28. Some observers believe that Qualcomm controls some 21% of LTE royalties.
President Barack Obama, during his recent visit to China, pushed his Chinese counterpart, Xi Jinping, on the use of Chinese antitrust policy to limit royalty fees for foreign companies. The push by Obama could alter China’s calculus on the issue, but it could just as well backfire. reports Fierce Wireless. It underscores the importance Washington places on China’s investigation.
The former deputy head of NDRC, Liu Tienan, was sentenced to life in prison earlier this month after convicting him of taking bribes and abusing his power, reports the NY Times.
China Mobile recently said it had 50 million LTE subscribers, with plans to have 150 million customers on the network by the end of next year and 300 million customers by the end of 2016. Their LTE network runs across a total of 130 megahertz of spectrum in the 1880-1900 MHz, 2320-2370 MHz and 2575-2635 MHz bands. China Unicom, the country’s No. 2 wireless carrier, said its 3G and LTE network attracted 4.9 million customers during Q3, while China Telecom, the country’s third-largest mobile operator, had 1.33 million LTE customers.
The latest edition of Ericsson’s Mobility Report predicts that 90 percent of the world’s population over six years old will have a mobile phone by 2020, with smartphone subscriptions forecast to top 6.1 billion by then.
Sprint & T-Mobile Charged with “Cramming”
Sprint & T-Mobile Charged with “Cramming”
Posted by
Sam Churchill
on
Sprint is facing a lawsuit by the Consumer Financial Protection Bureau that alleges the carrier illegally billed wireless consumers for tens of millions of dollars in unauthorized third-party charges.
The lawsuit contends that Sprint operated a billing system that allowed
third parties to bill for unwanted services, a process known as “cramming.”
T-Mobile has agreed to pay the FTC and FCC $90 million to settle cramming charges, according to the FCC’s site. An FTC and FCC investigation found T-Mobile guilty of breaking the law by “engaging in an unjust and unreasonable practice of billing consumers for products or services they had not authorized; and failing to provide a brief, clear, non-misleading, plain language description of the third-party charges.”
“Today we are suing Sprint for allowing illegal charges to be crammed onto consumers’ wireless bills,” CFPB Director Richard Cordray said in a statement. “Consumers ended up paying tens of millions of dollars in unauthorized charges, even though many of them had no idea that third parties could even place charges on their bills. As the use of mobile payments grows, we will continue to hold wireless carriers accountable for illegal third-party billing.”
The CPFB contends Sprint outsourced payment processing for digital purchases such as apps, games, books, movies, and music to vendors called “billing aggregators” without properly monitoring them. The lack of oversight, the lawsuit alleges, gave aggregators “near unfettered access to consumers’ wireless accounts,” according to a CPFB statement.
“Sprint’s system attracted and enabled unscrupulous merchants who, in some cases, only needed consumers’ phone numbers to cram illegitimate charges onto wireless bills,” the CPFB said. “The charges ranged from one-time fees of about $0.99 to $4.99 to monthly subscriptions that cost about $9.99 a month. Sprint received a 30-40 percent cut of the gross revenue from these charges.”
“We strongly disagree with (the CFPB’s) characterization of our business practices,” Sprint spokeswoman Stephanie Vinge Walsh said in a statement.
“It appears the CFPB has decided to use this issue as the test case on whether it has legal authority to assert jurisdiction over wireless carriers,” she said in an email.
Prodded by state attorneys general, Verizon, AT&T, Sprint and T-Mobile last year agreed to stop billing customers for third-party services.
The F.C.C. is conducting a similar investigation, and people close to the investigation said the parties were close to completing a settlement under which Sprint would pay $105 million in refunds and restitution for the unauthorized transactions.
T-Mobile has agreed to pay the FTC and FCC $90 million to settle cramming charges, according to the FCC’s site. An FTC and FCC investigation found T-Mobile guilty of breaking the law by “engaging in an unjust and unreasonable practice of billing consumers for products or services they had not authorized; and failing to provide a brief, clear, non-misleading, plain language description of the third-party charges.”
“Today we are suing Sprint for allowing illegal charges to be crammed onto consumers’ wireless bills,” CFPB Director Richard Cordray said in a statement. “Consumers ended up paying tens of millions of dollars in unauthorized charges, even though many of them had no idea that third parties could even place charges on their bills. As the use of mobile payments grows, we will continue to hold wireless carriers accountable for illegal third-party billing.”
The CPFB contends Sprint outsourced payment processing for digital purchases such as apps, games, books, movies, and music to vendors called “billing aggregators” without properly monitoring them. The lack of oversight, the lawsuit alleges, gave aggregators “near unfettered access to consumers’ wireless accounts,” according to a CPFB statement.
“Sprint’s system attracted and enabled unscrupulous merchants who, in some cases, only needed consumers’ phone numbers to cram illegitimate charges onto wireless bills,” the CPFB said. “The charges ranged from one-time fees of about $0.99 to $4.99 to monthly subscriptions that cost about $9.99 a month. Sprint received a 30-40 percent cut of the gross revenue from these charges.”
“We strongly disagree with (the CFPB’s) characterization of our business practices,” Sprint spokeswoman Stephanie Vinge Walsh said in a statement.
“It appears the CFPB has decided to use this issue as the test case on whether it has legal authority to assert jurisdiction over wireless carriers,” she said in an email.
Prodded by state attorneys general, Verizon, AT&T, Sprint and T-Mobile last year agreed to stop billing customers for third-party services.
The F.C.C. is conducting a similar investigation, and people close to the investigation said the parties were close to completing a settlement under which Sprint would pay $105 million in refunds and restitution for the unauthorized transactions.
Year-end US Carrier Coverage Report
Year-end US Carrier Coverage Report
Posted by
Sam Churchill
on
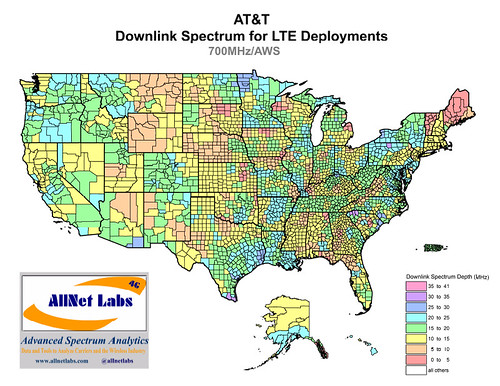
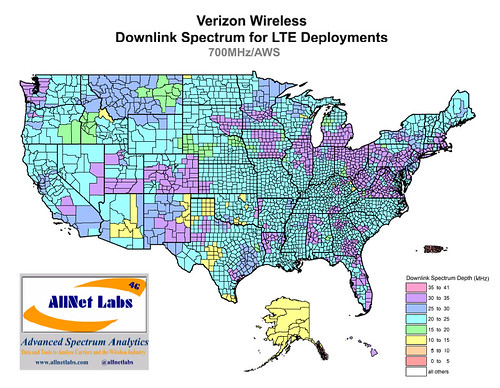
Verizon Wireless and AT&T Mobility say their 3G/4G coverage in the United States is now pretty much universal
with more than 300 million pops currently covered, mostly due to both
carrier’s extensive 700 MHz LTE networks. Now it’s a matter of keeping
up with capacity requirements.
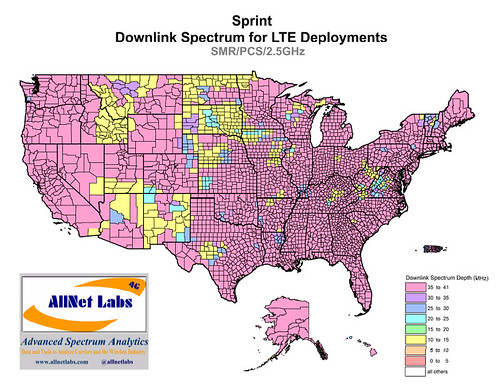
Sprint says its LTE network now covers 260 million people, mostly through the use of 10 megahertz of spectrum in the 1.9 GHz band. Next year, Sprint’s Chief Network Officer John Saw said Sprint will continue to build out its LTE network with its 800 MHz buildout about halfway finished. “We expect to be substantially complete with our LTE 800 MHz build by the end of 2015 in markets where the spectrum is available,” according to Saw.
Sprint’s 2.5 GHz coverage is now available in 62 markets, utilizing the carrier’s Spark program, reports Saw, which combines 800Mhz, 1.9GHz and 2.5 GHz. Their 2.5 GHz network covers about 100 million people.
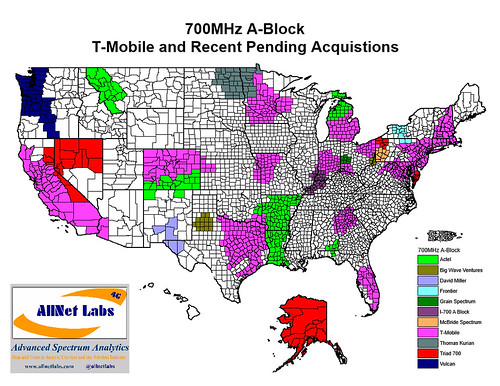
Meanwhile T-Mobile US CTO Neville Ray said the carrier’s LTE network coverage currently serves a similar 260 million pops, matching Sprint. Ray says T-Mobile is now on track to cover 280 million people with 4G LTE by mid-2015, and expects to hit the 300 million mark by the end of 2015.
T-Mobile has acquired more 700 MHz spectrum in the “A” block, reports FierceWireless, with the carrier making several deals for airwaves with small license holders in the last few months.
Sprint says its LTE network now covers 260 million people, mostly through the use of 10 megahertz of spectrum in the 1.9 GHz band. Next year, Sprint’s Chief Network Officer John Saw said Sprint will continue to build out its LTE network with its 800 MHz buildout about halfway finished. “We expect to be substantially complete with our LTE 800 MHz build by the end of 2015 in markets where the spectrum is available,” according to Saw.
Sprint’s 2.5 GHz coverage is now available in 62 markets, utilizing the carrier’s Spark program, reports Saw, which combines 800Mhz, 1.9GHz and 2.5 GHz. Their 2.5 GHz network covers about 100 million people.
Meanwhile T-Mobile US CTO Neville Ray said the carrier’s LTE network coverage currently serves a similar 260 million pops, matching Sprint. Ray says T-Mobile is now on track to cover 280 million people with 4G LTE by mid-2015, and expects to hit the 300 million mark by the end of 2015.
T-Mobile has acquired more 700 MHz spectrum in the “A” block, reports FierceWireless, with the carrier making several deals for airwaves with small license holders in the last few months.
Wednesday, November 19, 2014
McDonald’s Gets Softcard
McDonald’s Gets Softcard
Posted by
Sam Churchill
on
Softcard (formerly Isis), a mobile payment system that competes with Apple Pay and Google Wallet,
announced today that it is accepted at more than 14,000 McDonald’s
locations around the country beginning today. Smartphone owners can make
NFC-based mobile payments at the register and the drive-thru at all
McDonald’s restaurants. McDonald’s will also accept Apple Pay.
Last month, Subway also announced a partnership with Softcard to support mobile payments.
Softcard is free to download and is compatible with more than 80 Android handsets sold by AT&T, T-Mobile, and Verizon Wireless. Softcard combines payments, offers and loyalty in one app. Softcard uses the EMV Contactless specification and SmartTap technology to enable payments, offers and loyalty redemption through one tap.
Apple Pay saw more than one million card activations within 72 hours of launch, reports NFC World, and is already the leading NFC payments player in the US, according to Apple CEO Tim Cook. Cook outlined future growth plans for the service at the WS Journal D Live conference this week, including a potential partnership with Chinese ecommerce giant Alibaba.
 US pharmacy chains Rite Aid and CVS plan to launch their own CurrentC mobile payment service in 2015, and have stopped accepting NFC payments, blocking mobile payments services like Apple Pay, Google Wallet and Softcard.
US pharmacy chains Rite Aid and CVS plan to launch their own CurrentC mobile payment service in 2015, and have stopped accepting NFC payments, blocking mobile payments services like Apple Pay, Google Wallet and Softcard.
Unfortunately, CurrentC is now warning people that hackers have already swiped some of the beta tester’s email addresses.
Mobile proximity payments have to date proven lacklustre despite the hundreds of millions spent on developing these platforms. But loyalty rewards and benefits of the digital wallet is now seen by many as potentially the killer app that will help to finally ignite the long simmering mobile proximity payment market.
Ovum’s research indicates that 53% of consumers globally report they’ve either used or are interested in redeeming offers and coupons with their handsets, while 44% have used or are interested using their mobile device to pay for things in store and restaurants, explains Gilles Ubaghs, Senior Analyst, Financial Services Technology at Ovum.
source : dailywireless.org
Softcard is free to download and is compatible with more than 80 Android handsets sold by AT&T, T-Mobile, and Verizon Wireless. Softcard combines payments, offers and loyalty in one app. Softcard uses the EMV Contactless specification and SmartTap technology to enable payments, offers and loyalty redemption through one tap.
Apple Pay saw more than one million card activations within 72 hours of launch, reports NFC World, and is already the leading NFC payments player in the US, according to Apple CEO Tim Cook. Cook outlined future growth plans for the service at the WS Journal D Live conference this week, including a potential partnership with Chinese ecommerce giant Alibaba.
Unfortunately, CurrentC is now warning people that hackers have already swiped some of the beta tester’s email addresses.
Mobile proximity payments have to date proven lacklustre despite the hundreds of millions spent on developing these platforms. But loyalty rewards and benefits of the digital wallet is now seen by many as potentially the killer app that will help to finally ignite the long simmering mobile proximity payment market.
Ovum’s research indicates that 53% of consumers globally report they’ve either used or are interested in redeeming offers and coupons with their handsets, while 44% have used or are interested using their mobile device to pay for things in store and restaurants, explains Gilles Ubaghs, Senior Analyst, Financial Services Technology at Ovum.
source : dailywireless.org
AT&T Verizon Work Toward VoLTE Interoperability
AT&T & Verizon Work Toward VoLTE Interoperability
Posted by
Sam Churchill
on
Verizon and AT&T are working to enable Voice over LTE interoperability, reports Fierce Wireless. The two carriers said they are going to enable VoLTE-to-VoLTE connections in 2015. Voice over LTE (VoLTE) was devised to standardise a method for transferring voice over LTE data networks.
According to a Verizon blog post, engineers from both companies will start with lab testing and then move to field trials next year. Verizon said customers will have a seamless experience making VoLTE HD Voice calls between the two networks as well as other Rich Communications Services (RCS) such as video calls, rich messaging and more.
T-Mobile, meanwhile, has VoLTE available in more than a dozen cities (with the proper phone), and has been testing interoperability, with interop agreements with VerizonWireless and Sprint since May, notes John Legere.
 AT&T introduced VoLTE services in its initial markets earlier this year,
and will continue to expand to more devices and more markets across the
United States. “Interoperability of VoLTE between wireless carriers is
crucial to a positive customer experience,” said Krish Prabhu, president, AT&T Labs and Chief Technology Officer, AT&T.
AT&T introduced VoLTE services in its initial markets earlier this year,
and will continue to expand to more devices and more markets across the
United States. “Interoperability of VoLTE between wireless carriers is
crucial to a positive customer experience,” said Krish Prabhu, president, AT&T Labs and Chief Technology Officer, AT&T.
Currently, to experience Verizon’s VoLTE service both parties on a call need to be using a VoLTE-enabled Verizon smartphone. AT&T’s VoLTE-enabled HD Voice service lets customers only make HD Voice calls with other AT&T customers using AT&T HD Voice-capable devices within AT&T HD Voice coverage areas.
An additional requirement for VoLTE enabled networks is to have a means to handing back to circuit switched legacy networks in a seamless manner, while only having one transmitting radio in the handset to preserve battery life. A system known as Single Radio Voice Call Continuity (SRVCC) is required for this. Handover from LTE to the legacy network is required when the user moves out of the LTE coverage area.
The benefit to wireless operators is more-efficient use of their network resources, explains C/Net’s Maggie Reardon. VoLTE benefits for consumers include faster call setup times (twice as fast as a non-VoLTE call setup), LTE data speeds while you are on a call, and HD Voice service with greater call quality.
source : dailywireless.org
According to a Verizon blog post, engineers from both companies will start with lab testing and then move to field trials next year. Verizon said customers will have a seamless experience making VoLTE HD Voice calls between the two networks as well as other Rich Communications Services (RCS) such as video calls, rich messaging and more.
T-Mobile, meanwhile, has VoLTE available in more than a dozen cities (with the proper phone), and has been testing interoperability, with interop agreements with VerizonWireless and Sprint since May, notes John Legere.
 AT&T introduced VoLTE services in its initial markets earlier this year,
and will continue to expand to more devices and more markets across the
United States. “Interoperability of VoLTE between wireless carriers is
crucial to a positive customer experience,” said Krish Prabhu, president, AT&T Labs and Chief Technology Officer, AT&T.
AT&T introduced VoLTE services in its initial markets earlier this year,
and will continue to expand to more devices and more markets across the
United States. “Interoperability of VoLTE between wireless carriers is
crucial to a positive customer experience,” said Krish Prabhu, president, AT&T Labs and Chief Technology Officer, AT&T. Currently, to experience Verizon’s VoLTE service both parties on a call need to be using a VoLTE-enabled Verizon smartphone. AT&T’s VoLTE-enabled HD Voice service lets customers only make HD Voice calls with other AT&T customers using AT&T HD Voice-capable devices within AT&T HD Voice coverage areas.
An additional requirement for VoLTE enabled networks is to have a means to handing back to circuit switched legacy networks in a seamless manner, while only having one transmitting radio in the handset to preserve battery life. A system known as Single Radio Voice Call Continuity (SRVCC) is required for this. Handover from LTE to the legacy network is required when the user moves out of the LTE coverage area.
The benefit to wireless operators is more-efficient use of their network resources, explains C/Net’s Maggie Reardon. VoLTE benefits for consumers include faster call setup times (twice as fast as a non-VoLTE call setup), LTE data speeds while you are on a call, and HD Voice service with greater call quality.
source : dailywireless.org
Tuesday, June 3, 2014
Wednesday, February 19, 2014
Executive Cyber Intelligence Bi-Weekly Report by INSS-CSFI February 1st, 2014
Executive Cyber Intelligence Bi-Weekly Report by INSS-CSFI
February 1st, 2014
Israel
Cyber Park in Beer Sheba expandingOne of the biggest network companies, Cisco, will invest millions of dollars in the Israeli cyber industry through the JVP foundation, The Marker reported. This investment joins the announcement made by Lockheed Martin and EMC on opening a research center/cyber park in Beer Sheba (initial investment being one million dollars). The park will be called Cyber-Spark and will accommodate leading cyber industries, academic research, and the national cyber command. Another addition to the ever growing park will be made by IBM in cooperation with Ben Gurion University, who declared their intention to open a center for global excellence in the field of cyberspace. The rise of the cyber industry in Beer Sheba is meant to create a cyber hub in the middle of the South, as well as mixing economic and security growth by creating 15,000 jobs in a few years.
Israel’s Darknet and TOR dilemma
Last year, Edward Snowden turned over to The Guardian 58,000 classified U.S. government documents, and only a fraction of the files have been made public. To avoid detection, Snowden almost certainly relied on one very specific and powerful tool to cover his tracks – TOR. TOR, an acronym for “the onion router,” is software providing the closest thing to anonymity on the Internet. Engineered by the TOR Project, TOR has been adopted by both agitators for liberty and criminals, and many people who use TOR do so to browse the Darknet liberally. Many countries have faced questions on how to deal with Darknet, and an example occurred with two young men in Israel, standing trial for using Bitcoins to purchase drugs on the Darknet. The young men also used fake credit card numbers, which were bought through the Darknet. This criminal issue related to Darknet is one of several cases the Israel court has had to deal with in the past few months.
USA
Changes in NSA and cyber security matters due to Snowden affairGeneral Keith Alexander, Director of the NSA, is stepping down and being replaced by U.S. Navy’s Cyber Security Chief, Michael S. Rogers. Since whistle-blower Edward Snowden revealed the intensity of U.S. spying on its citizens and allies, a call has been made for intelligence agencies to be more transparent and for them to uphold the law. The U.S. has faced many embarrassments and the need for explanation since the Edward Snowden affair. Yet because of the Snowden affair, policy decisions in cyber security have reached a stalemate as the U.S. has begun struggling to deal with the daily cyber-attacks from Russia and China. Plans and projects in the NSA have halted even though ideas could be effective, and decision makers in Congress explain: “[Snowden] slowed everything down.” However, opposing and pro-Snowden supporters insist the problem in U.S. and fighting terrorism was never lack of information but U.S. intelligence agencies not sharing data or informing the public. As it currently stands, the FBI, NSA, and DHS are denied to share classified cyberspace information with the civilian population. Since Snowden, the U.S. has faced growing criticism internationally, with foreign leaders disregarding Obama’s warnings regarding cyber affairs. The announcement of Rogers as Director of NSA comes a few days after the cyber hackers group Anonymous hacked and publicized email addresses of U.S. members of the Federal Bureau Investigation.
Microsoft answers to growing criticism
Microsoft has responded to breaches in its security when it announced plans to launch ‘Transparency Centers’ worldwide, enabling government customers to verify their Microsoft products. Microsoft has faced growing pressure and criticism over its involvement with U.S. spying after the revelations of Edward Snowden Prism, a top-secret program giving the NSA direct access to the systems of Google, Microsoft, and Facebook. Microsoft also faced the embarrassment of being hacked by the SEA through phishing attempts on Microsoft email accounts to steal information. Microsoft plans to expand encryption across its services to provide legal protection for customer’s data and government users. Plans to reveal the source code have remained unannounced.USA: Major retailers in the U.S. hacked during holiday season
Massive cyber-attacks hit major U.S. retail stores of high end Neiman Marcus. Neiman Marcus confirmed a data breach involving credit card theft from customers during the holiday shopping season, where hackers rooted payment information from customers. Neiman Marcus spokesperson, Ginger Reeder, stated the company is unaware of the cause or identification of the data breach, but they informed “federal law enforcement agencies and are working actively with the U.S. Secret Service, the payment brands, our credit card processor, a leading investigations, intelligence and risk management firm, and a leading forensic firm to investigate the situation.” Similar breaches affected Target on Black Friday, the biggest shopping day in the U.S. Senator Edward J. Markey (D-Mass) responded to the attack stating: “In the wake of the Target breach, customers, lawmakers, and consumer advocates have stepped up calls for Congress to set up guidelines on how merchants should protect consumer data…a need for clear, strong privacy and security standards across all industries.” Target has already responded with CEO Gregg Steinhafel proclaiming to improve Target’s understanding of consumer-based scams, including removing the malware the cyber criminals installed, hiring a team of data security to investigate occurrence, and working with law enforcement. Target is also preparing to announce an education campaign on accelerating the knowledge on technology and cyber security. Some believe other retail stores have been affected, causing a pattern in attacks heading towards larger widespread attacks. Chris Petersen, CTO of LogRythm remarked that this would entail extremely sophisticated malware software. At this time, these are just rumours circulating, and IntelCrawler contended the attacks on Target and Neiman Marcus were separate. Nevertheless, no national breach disclosure law exists, allowing many companies who may have been attacked to not publicize it.Russia
Russia to set up a cyber-defense unit
Russian Maj. Gen. Yuri Kuznetsov was quoted by the national news agency RIA Novosti, stating a cyber-defense unit will be ready “to defend the Russian armed forces’ critical infrastructure from computer attacks” by 2017. The mission maintains to better protect the defense sector from cyber-attacks. Cyber-warfare has emerged and has become a national security threat in recent years to Russia. Websites used by Asian governments were targeted by the “Anonymous” cybercrime organization in 2013, and U.S. and Chinese officials have traded accusations about cyber espionage in recent years. RIA Novosti reports the Russian newspaper Vedomosti was knocked offline Thursday by a DDoS cyber-attack (denial-of-service), overwhelming servers with requests. Alexei Moshkov, Russia’s top cybercrime official, claimed cyber-attacks last year on Russian citizens combined cost around $28 million.Middle East & Iran
Palestinian hackers suspected to be behind breach in Israeli defense ministry computers
Hackers broke into Israeli defense ministry computers by sending phishing e-mails containing an advanced remote access Trojan called Xtreme Rat, Aviv Raff, CTO of Seculert Research Lab, blogged on January 27th. The e-mail appeared as if it was sent by the Israeli Security Agency enabling legitimacy, and the original target was Israeli Customs, according to TrendMicro. One of the 15 breached computers revealed to be Israeli Civil Administration of Judea and Samaria, which monitors entry and work permits into the West Bank from Israel. The Civil Administration made no comment in regards to an attack. Even though the attack was conducted from a server located within the U.S., similarities in code to past cyber-attacks conducted from a Hamas server on the Israeli Police, enhanced rumours the Palestinians were behind the cyber-attack. As of now, it is unclear if the hackers used or gained any information.Saudi Arabia to launch National e-Security Center to Protect Government against Hackers
Saudi Arabia embarked on producing a national authority for information security called the National e-Security Center. The main goal will be to protect important networks against cyber-attacks. The decision came after numerous attacks were launched by both cybercriminals and hacktivist on the Saudi Arabian government websites. An example was when the Saudi Arabian Interior Ministry was breached with a DDoS attack, disrupting the website for several hours in May. The attack was traced back to various countries.
Iran unveils new cyber security products
Fars news agency reported Iran was unveiling 12 new Iranian technological products within the cyber field at a ceremony held and attended by Iranian Defense Minister Brigadier General Hossein Dehqan and Head of Iran’s Civil Defense Organization Brigadier General Gholam Reza Jalali. Among the products revealed was a cell phone providing secure communications, immune from tapping. Other products unveiled were a home-made, secure operating system, a indigenized navigation system, a telecommunications optical transmission system, Padvish anti-malware, a cyber threats recognition and identification system, a security operations center, a high-speed and high-capacity firewall, and a software firewall.
Iran has launched an indigenous cyber defense network cited as “Shahpad,” according to project manager Mohammad Naderi. The initial idea stemmed from missile defense shields used in different countries to prevent missile attacks. “Shahpad” is the outcome of several years of research. The system protects data, operates as a data manager, and is responsive to the safety needs of all organizations. According to Iranian news agency ISNA, whenever a threat against an organization is detected, the system informs other sensors using smart mechanisms for the exchange of intelligence. The system is capable of informing all sensitive and important agencies such as Security Operations Centers across the country, facilitating a swift reaction.
SEA attacks PayPal UK and eBay UK
The Syrian Electric Army (SEA) used a DDoS cyber-attack on PayPal UK and eBay UK, causing Twitter to shut down the SEA’s official Twitter handle. Both PayPal UK and eBay UK verified the attacks occurred, and they were resolved shortly afterwards; however, they made no mention of the crude defacement SEA had left on their webpages with messages: “Hacked by the Syrian Electronic Army. Long live Syria. F*ck the United States government.” SEA stated the cyber-attack occurred because of PayPal’s denial to allow Syrians to purchase products online and also assured no information had been gathered by the account, unlike previous cyber-attacks were it was documented the SEA had stolen law enforcement data from Microsoft.
China and APAC
Japan sending Self Defense Forces to U.S. for cyber training
The Japanese government will send members of its Self-Defense Forces (SDF) to receive specialized training in cyber defense with U.S. forces in a cooperative program to bolster Japan’s defense against cyber-attacks, sources said. The SDF members will learn from technologies and experiences of the more advanced U.S. forces in countering cyber-attacks. The project aims to improve the SDF’s cyber defense capabilities and to strengthen Japan-U.S. cooperation. Until today, the Japan-U.S. cooperation in the field of cyber-defense was limited to exchanging information; however, this project is expected to strengthen the collaboration between the two countries.
Europe
Europol smashed financial cyber-crime gang targeting UK citizensThe European cyber-crime agency EC3 of Europol was thanked after Polish police arrested five Bulgarian citizens accused of electronic payment card fraud targeting mainly UK citizens. The agency declared three hackers from the gang were caught, two of them were carrying out illegal electronic payment card transactions at automated cash machines (ATMs). One of them was receiving compromised card numbers online and encoding counterfeit plastic cards. The other two suspects were arrested in different hotels in Krakow on 22 January. Europol said the financial data involved came mainly from the U.K., but a spokesperson informed to online security magazine SCMagazineUK.com that they could not divulge about the UK card holders involved as “the investigation is still ongoing.” The European cybercrime center was created a year ago, and its role is to help to co-ordinate national police forces targeting cyber criminals all over Europe.
Germany: Increase of Cyber Attacks
A study conducted by the Federal Office for Information Security (BSI) in Germany recorded 2,000 to 3,000 attacks on the German government Internet domains per day. Some cyber-attacks are on such an advanced technical level, the alleged offenders are suspected to be intelligence services. Hundreds of thousands of computers in Germany are infiltrated and potentially could be operated for cyber-attacks through so-called bot networks by remote control, making computers used as tools for crime without the knowledge of the actual owner. Many German companies experience cyber-attacks; however, instead of reporting these offenses, companies conceal them to avoid damage control.
The Federal Criminal Police Office counted almost 64,000 cases of cyber-crime solely in Germany, raising concerns with security experts. According to the EU, more than a million people fall victim to cyber-attacks each day, ranging from hacked bank transfers to digital blackmail to dispersal of child pornography. At this point, the President of BSI Michael Hange expressed the relevance to sensitize and educate the public in IT security. The President of the Federal Academy for Security Politics Hans-Dieter Hermann spoke about a confidence crisis and how European states must realize their standards.
 About the Cyber Intelligence Report:
About the Cyber Intelligence Report:
This document was prepared by The Institute for National Security Studies (INSS)
– Israel and The Cyber Security Forum Initiative (CSFI) – USA to create
better cyber situational awareness (Cyber SA) of the nature and scope
of threats and hazards to national security worldwide in the domains of
cyberspace and open source intelligence. It is provided to Federal,
State, Local, Tribal, Territorial and private sector officials to aid in
the identification and development of appropriate actions, priorities,
and follow-on measures. This product may contain U.S. person information
that has been deemed necessary for the intended recipient to
understand, assess, or act on the information provided. It should be
handled in accordance with the recipient’s intelligence oversight and/or
information handling procedures. Some content may be copyrighted. These
materials, including copyrighted materials, are intended for “fair use”
as permitted under Title 17, Section 107 of the United States Code
(“The Copyright Law”). Use of copyrighted material for unauthorized
purposes requires permission from the copyright owner. Any feedback
regarding this report or requests for changes to the distribution list
should be directed to the Open Source Enterprise via unclassified e-mail
at: inssdcoi@gmail.com. CSFI and the INSS would like to thank the Cyber Intelligence Analysts who worked on collecting and summarizing this report.
Mobile World Congress: What to Expect
Mobile World Congress: What to Expect
Posted by Sam Churchill on
Mobile World Congress, the world’s largest mobile show, starts on the 24th (, exhibitors and Mobile World Daily).
A plethora of smartphone, tablet, wearable, and infrastructure announcements are expected and reported on (twitter, facebook, YouTube, IOS App and Android App).
A plethora of smartphone, tablet, wearable, and infrastructure announcements are expected and reported on (twitter, facebook, YouTube, IOS App and Android App).
Smartphone and tablet announcements
- Samsung: At CES Samsung announced two tablets: the Galaxy TabPro and the Galaxy NotePro. A big Samsung event on February 24, is rumored to announce the new flagship S-5 smartphone. It is expected to feature a fingerprint reader on the home button. Phones based on Tizen, an alternative operating system to Android, are also rumored.
- LG: LG has announced three new smartphones called the L90, L70 and L40 which will become the L Series III from LG. It follows up the L Series and L Series II. The flagship G3, a G Pro 2 phablet, and a watch are also rumored. The G3 may have a 2.2GHz octa-core run Android 4.4 KitKat, 2560 x 1440 pixel resolution, and feature a fingerprint scanner. The LG G2 Pro will feature a 13MP camera with improved optical image stabilization (OIS+) and 4K (3840 x 2160 pixels) video recording.
- HTC The 5.5-inch HTC Desire 8 will be formally unveiled next week while the flagship HTC One 2 is expected to have its own dedicated launch event in March. HTC could also announce a line of mid-range devices.
- Huawei a new smartphone, two new tablets, and most interestingly, a smartwatch are expected from the manufacturer. Specs, or other details are still few.
- Motorola No new hardware, but there could be some details about how the Lenovo purchase of Motorola will work and what it means for the future of the company.
- Nokia: The Lumia 930 would be the successor to the Nokia Lumia 920 and would launch with a quad-core 2.2GHz processor and 2GB of RAM. Nokia’s event could include an 8-inch tablet – possibly the Lumia 2020, but the really interesting rumors are of an Android smartphone.
- Sony: According to rumors, there will be a new flagship phone – the 5.2-inch Sirius or Xperia Z2 at MWC, and possibly a Sony Castor tablet to update the Xperia Tablet Z.
- ZTE: The Chinese gian showed off the Grand S2, a couple of Nubia phones, and the Sonata 4G at CES. Announcements at MWC could add Tizen phones and smartwatches to the lineup. The ZTE Geek is the first ZTE smartphone to sport an Intel processor (the new 32nm Atom Z2580).
Infrastructure announcements
- Alcatel-Lucent: Small Cells, WiFi 2.0 Integration, LTE-Advanced and new LTE wins are expected. Alcatel-Lucent will showcase a new Distributed Antenna System. The U.S. and China are the world’s largest DAS markets and are expected to remain so through at least 2017.
- Ericsson: The largest cellular infrastructure company will likely have announcements across the board, including their new 4G-compatible cloud-based push-to-talk (PTT) service in Europe.
- NSN: Announcements on 5G, Mobile Broadband/LTE, Big data, OTT, telco cloud and outsourcing are promised.
- Huawei: Huawei is promoting its FusionSphere — an open cloud platform optimized for convergence. Huawei’s Cloud DC solution flattens architecture to facilitate global management & resource scheduling.
Reconnaissance Aircraft Monitor Flooded Areas over Southern England
Stormy weather and unprecedented rainfall over the UK is causing
floods throughout southern England, some areas have been flooded for
several weeks. As 14 severe flood warnings remain in place along the
Thames, Berkshire and Surrey, and two in the Somerset Levels, the
military is called to help local communities fighting the rising water
in an effort to protect property and restore routine life.

 More than 3,000 military
personnel have already joined flood relief efforts, and 5,000 more are
preparing to help flood-stricken communities. “We’ve got to treat it
like any other national security issue” Labour leader Ed Miliband said,
describing the floods and climate change in general as a “national
security issue” for the UK.
More than 3,000 military
personnel have already joined flood relief efforts, and 5,000 more are
preparing to help flood-stricken communities. “We’ve got to treat it
like any other national security issue” Labour leader Ed Miliband said,
describing the floods and climate change in general as a “national
security issue” for the UK.
While soldiers creating sandbag walls and flood defense are a regular view in the flood stricken areas, the RAF has provided additional support from above, committing surveillance aircraft to provide authorities a unique picture of the situation on the ground.
 Two of the assets employed include surveillance patrols Sentinel R1 employing synthetic aperture radar (SAR)
clearly indicating the wet and flooded areas over wide areas of land.
With mapping provided the Sentinel, the RAF could deploy Tornado strike
fighters carrying RAPTOR electro-optical reconnaissance pods, to bring
visual reconnaissance from the affected areas. The combination of wide
area surveillance and reconnaissance delivered by fast jets could
process a situational picture of the wide area affected by the storm and
floods, enabling authorities to focus on the worst affected areas.
Two of the assets employed include surveillance patrols Sentinel R1 employing synthetic aperture radar (SAR)
clearly indicating the wet and flooded areas over wide areas of land.
With mapping provided the Sentinel, the RAF could deploy Tornado strike
fighters carrying RAPTOR electro-optical reconnaissance pods, to bring
visual reconnaissance from the affected areas. The combination of wide
area surveillance and reconnaissance delivered by fast jets could
process a situational picture of the wide area affected by the storm and
floods, enabling authorities to focus on the worst affected areas.
By using the imagery gathered by both systems, civilian authorities will be able to compare the current flooding in the Thames Valley to how the same area was affected during a similar devastating period of flooding in 1947 which was caused by melting snow and extended periods of heavy rain. Being able to draw comparisons may help to indicate what areas are most likely to be affected next and help the civilian authorities to make informed decisions about where best to target their efforts.
“The Sentinel has long-range capabilities which enable highly trained Airborne Image Analysts onboard to capture imagery of large parts of the flooded areas.” Squadron Leader Victoria Fulton, Chief of Staff 5 (Army Co-operation) Squadron saID, “It is hoped that this key information will greatly assist the civilian authorities when determining where best to focus their efforts.”
The Tornado aircraft and RAPTOR has been used in many military operations and is currently in use over Afghanistan. It was selected for this task as it can rapidly scan and capture a huge area of interest in just one sortie – in this case areas in need of flood relief work.
“The sortie launched today demonstrates the versatility of both the [Tornado] aircraft and its reconnaissance systems and of the men and women who support those operations.” Wing Commander Neil Tomlin, Acting Station Commander said, “It is hoped that the imagery provided by our RAPTOR reconnaissance system will provide valuable assistance in supporting the flood relief efforts currently under way in the South of England.”

 No 5(Army Cooperation) Squadron operates the Advanced Stand Of Radar (ASTOR) radar surveillance system, and comprises 5 Sentinel R1
aircraft and 8 Ground Stations. The concept of the ASTOR system is to
provide a highly effective 24-hour surveillance and target acquisition
capability. It delivers wide area, all-weather, tactical, theatre and
national surveillance information in near real time. At its heart is a
dual mode Synthetic Aperture/Moving Target Indicator (SAR/MTI)
radar. The SAR provides high-resolution images and the MTI monitors
hostile forces – their quantity, direction and speed. The imagery can be
exploited both on board the aircraft and on the ground, is passed to
Ground Stations at both theatre and tactical level. By operating at high
altitude and considerable stand-off distances, the radar platform is
able to remain over safe territory while providing an excellent
‘look-down’ angle of the target area.
No 5(Army Cooperation) Squadron operates the Advanced Stand Of Radar (ASTOR) radar surveillance system, and comprises 5 Sentinel R1
aircraft and 8 Ground Stations. The concept of the ASTOR system is to
provide a highly effective 24-hour surveillance and target acquisition
capability. It delivers wide area, all-weather, tactical, theatre and
national surveillance information in near real time. At its heart is a
dual mode Synthetic Aperture/Moving Target Indicator (SAR/MTI)
radar. The SAR provides high-resolution images and the MTI monitors
hostile forces – their quantity, direction and speed. The imagery can be
exploited both on board the aircraft and on the ground, is passed to
Ground Stations at both theatre and tactical level. By operating at high
altitude and considerable stand-off distances, the radar platform is
able to remain over safe territory while providing an excellent
‘look-down’ angle of the target area.

Soldiers
have been working in Staines putting up a dam in a field to redirect
water away from housing into fields. The soldiers are from C company
Royal Ghurka Rifles. Photo: Crown Copyright
The
deployment of the Tornado GR4 from RAF Marham in Norfolk has produced
detailed imagery that will aid the planning and co-ordination of
multi-agency efforts to provide relief to local residents and
communities. Photo: Crown Copyright
While soldiers creating sandbag walls and flood defense are a regular view in the flood stricken areas, the RAF has provided additional support from above, committing surveillance aircraft to provide authorities a unique picture of the situation on the ground.
Flooded
area analysis of the Thames Valley and Hampshire, UK generated by SAR
imaging provided by Sentinel R1 sortie over Somerset. The Sentinel was
operated by the RAF’s 5 (Army Cooperation) Squadron from RAF Waddington
in Lincolnshire. Photo: Crown Copyright
By using the imagery gathered by both systems, civilian authorities will be able to compare the current flooding in the Thames Valley to how the same area was affected during a similar devastating period of flooding in 1947 which was caused by melting snow and extended periods of heavy rain. Being able to draw comparisons may help to indicate what areas are most likely to be affected next and help the civilian authorities to make informed decisions about where best to target their efforts.
“The Sentinel has long-range capabilities which enable highly trained Airborne Image Analysts onboard to capture imagery of large parts of the flooded areas.” Squadron Leader Victoria Fulton, Chief of Staff 5 (Army Co-operation) Squadron saID, “It is hoped that this key information will greatly assist the civilian authorities when determining where best to focus their efforts.”
The Tornado aircraft and RAPTOR has been used in many military operations and is currently in use over Afghanistan. It was selected for this task as it can rapidly scan and capture a huge area of interest in just one sortie – in this case areas in need of flood relief work.
“The sortie launched today demonstrates the versatility of both the [Tornado] aircraft and its reconnaissance systems and of the men and women who support those operations.” Wing Commander Neil Tomlin, Acting Station Commander said, “It is hoped that the imagery provided by our RAPTOR reconnaissance system will provide valuable assistance in supporting the flood relief efforts currently under way in the South of England.”
The
Royal Air Force launched one of its Tornado strike fighters on Thursday
February 23, 2014 to capture a highly detailed aerial picture of the
areas affected by the floods in southern England, after a request by
Gold commanders in the Thames Valley. The aircraft, operated by the
RAF’s 31 Squadron, is equipped with the highly versatile RAPTOR –
Reconnaissance Air Pod for Tornado – which enables it to gather
high-resolution imagery. Photo: Crown Copyright
The air crew of the Sentinel monitoring surveillance images collected in flight. Photo: UK MOD, Crown Copyright
Sentinel R1 aircraft operated by No 5 Squadron. Photo: UK MOD, Crown Copyright
Subscribe to:
Comments (Atom)