Infrastructure War
Posted by samc on January 21st, 2008The CIA on Friday admitted that cyberattacks have caused at least one power outage affecting multiple cities outside the United States.
Alan Paller, director of research at the SANS Institute, said that CIA senior analyst Tom Donahue confirmed that online attackers had caused at least one blackout. The disclosure was made at a New Orleans security conference Friday attended by international government officials, engineers, and security managers from North American energy companies and utilities.
According to analyst Donahue, “We have information, from multiple regions outside the United States, of cyber intrusions into utilities, followed by extortion demands. We suspect, but cannot confirm, that some of these attackers had the benefit of inside knowledge. We have information that cyberattacks have been used to disrupt power equipment in several regions outside the United States. In at least one case, the disruption caused a power outage affecting multiple cities. We do not know who executed these attacks or why, but all involved intrusions through the Internet.”
Delegates at the security meeting shared information on how attackers are eluding current defenses and on promising practices for mitigating the most critical vulnerabilities. They also shared a jointly developed “SCADA and Control Systems Survival Kit.”
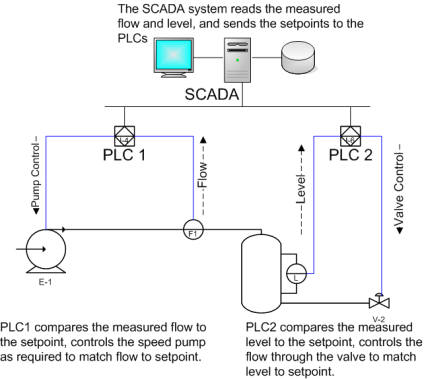
The Department of Energy established the National Supervisory Control and Data Acquisition (SCADA) Test Bed program at Idaho National Laboratory and Sandia National Laboratory.
SCADA (Supervisory Control And Data Acquisition) systems control critical infrastructures — such as electric power generators, traffic signals, dams, and other systems. Here are 21 Steps to improve SCADA security:
1. Identify all connections to SCADA networks.
2. Disconnect unnecessary connections to the SCADA network
3. Evaluate and strengthen the security of any remaining connections to the SCADA network
4. Harden SCADA networks by removing or disabling unnecessary services
5. Do not rely on proprietary protocols to protect your system
6. Implement the security features provided by device and system vendors
7. Establish strong controls over any medium that is used as a backdoor into the SCADA network
8. Implement internal and external intrusion detection systems and establish 24-hour-a-day
incident monitoring
9. Perform technical audits of SCADA devices and networks, and any other connected
networks, to identify security concerns
10. Conduct physical security surveys and assess all remote sites connected to the
SCADA network to evaluate their security
11. Establish SCADA “Red Teams” to identify and evaluate possible attack scenarios
12. Clearly define cyber security roles, responsibilities, and authorities for managers,
system administrators, and users
13. Document network architecture and identify systems that serve critical functions
or contain sensitive information that require additional levels of protection
14. Establish a rigorous, ongoing risk management process
15. Establish a network protection strategy based on the principle of defense-in-depth
16. Clearly identify cyber security requirements
17. Establish effective configuration management processes
18. Conduct routine self-assessments
19. Establish system backups and disaster recovery plans
20. Senior organizational leadership should establish expectations for cyber security
performance and hold individuals accountable for their performance
21. Establish policies and conduct training to minimize the likelihood that organizational
personnel will inadvertently disclose sensitive information regarding SCADA system
design, operations, or security controls
Cyber espionage is getting renewed attention. The SANS Institute ranks cyber espionage No. 3 on its Top Ten Cyber Menaces for 2008”,” just behind Web site attacks exploiting browser vulnerabilities and botnets. Twelve noted cybersecurity experts — Stephen Northcutt, Ed Skoudis, Marc Sachs, Johannes Ullrich, Tom Liston, Eric Cole, Eugene Schultz, Rohit Dhamankar, Amit Yoran, Howard Schmidt, Will Pelgrin, and Alan Paller — helped compile The Top 10 Threat List:
- Increasingly Sophisticated Web Site Attacks That Exploit Browser Vulnerabilities - Especially On Trusted Web Sites.
Web site attacks on browsers are increasingly targeting components, such as Flash and QuickTime, that are not automatically patched when the browser is patched.
- Increasing Sophistication And Effectiveness In Botnets.
The so-called Storm worm (which was not really a worm at all) started spreading in January, 2007 with an email saying, “230 dead as storm batters Europe,” and was followed by subsequent variants. Within a week it accounted for one out of every twelve infections on the Internet.
- Cyber Espionage Efforts By Well Resourced Organizations Looking To Extract Large Amounts Of Data - Particularly Using Targeted Phishing.
One of the biggest security stories of 2007 was disclosure in Congressional hearings and by senior DoD officials of massive penetration of federal agencies and defense contractors and theft of terabytes of data by the Chinese and other nation states.
- Mobile Phone Threats, Especially Against iPhones And Android-Based Phones; Plus VOIP.
Mobile phones are general purpose computers, so worms, viruses, and other malware will increasingly target them. Attacks on VoIP systems are on the horizon and may surge in 2008.
- Insider Attacks.
Insider attacks are initiated by rogue employees, consultants and/or contractors of an organization.
- Advanced Identity Theft from Persistent Bots.
A new generation of identity theft is being powered by bots that stay on machines for three to five months collecting passwords, bank account information, surfing history, frequently used email addresses, and more. They’ll gather enough data to enable extortion attempts (against people who surf child porn sites, for example) and advanced identify theft attempts where criminals have enough data to pass basic security checks.
- Increasingly Malicious Spyware.
Criminal and nation-state attackers continue to refine the capabilities of their malicious code, expanding on flux techniques to obscure their infrastructure, making it even harder to locate their servers.
- Web Application Security Exploits.
Large percentages of web sites have cross site scripting, SQL injection, and other vulnerabilities resulting from programming errors. In 2008, web 2.0 vulnerabilities will be added to more traditional programming flaws and web application attacks will grow substantially.
- Increasingly Sophisticated Social Engineering Including Blending Phishing with VOIP and Event Phishing.
Blended approaches will amplify the impact of many more common attacks.
- Supply Chain Attacks Infecting Consumer Devices (USB Thumb Drives, GPS Systems, Photo Frames, etc.) Distributed by Trusted Organizations.
Retail outlets are increasingly becoming unwitting distributors of malware. Devices with USB connections and the CDs packaged with those devices sometimes contain malware that infect victims’ computers and connect them into botnets.
In related news, the RIAA Website was Wiped Clean by “Hackers” last week. According to Torrent Freak:
Apparently the RIAA is so busy suing consumers that they forgot to hire a decent programmer. With a simple SQL injection, all their propaganda has been successfully wiped from the site.
 Hackers armed with a Web browser and a rigged SWF (Shockwave) file can fire code execution exploits at most modern Wi-Fi routers, according to a warning from researchers at the GNUCITIZEN think-tank.
Hackers armed with a Web browser and a rigged SWF (Shockwave) file can fire code execution exploits at most modern Wi-Fi routers, according to a warning from researchers at the GNUCITIZEN think-tank.
The researchers, Adrian Pastor and Petko D. Petkov (right), have found an easy way to use Shockwave files embedded on Web pages to silently launch a four-step attack to take control of any router that use the UPnP (Universal Plug and Play) protocol. Petkov said the attack would work against “99 percent of all routers” running around the world. “Using what we know, it is trivial to construct a massive router botnet,” Petkov declared.
Honeypots and Evil Twins are two other significant WiFi threats. WiFi Planet links to additional articles on the subject. E-Week’s Security Watch has a fast rundown of other current security issues.
DailyWireless has more on The Cold War in Space and the rash of fiber optic cuts that have transpired over the last week, some due to storms, some due to vandalism.
source : dailywireless.org



No comments:
Post a Comment